personal computing


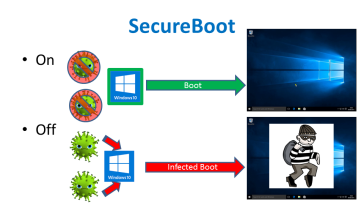
What is secure boot on Windows
For a long time now, viruses have been a major concern for computer users. You not only risk losing your data, you also risk having your privacy compromised when attacked by Viruses and Malware. Microsoft Secure Boot is a component of Microsoft's Windows 8 operating... Read More

Advertisement




Is Wireless Charging coming to your laptop?
Is wireless charging coming to your laptop? This is a question that would've (maybe) seem quite unreasonable to ask a couple of years ago. However, since original equipment manufacturers (OEMs) have begun featuring the wireless charging technology on premium high-end flagship smartphones for over 2 years... Read More

WhatsApp scam: How to prevent your privacy from being compromised
Whatsapp has over one billion users in about 180 countries all over the world. This messaging platform allows the users to make calls, share videos and send text messages. However hackers and fraud stars have developed new strategies to send viruses and compromise your privacy... Read More

Advertisement
The difference Between GPT vs MBR and which one you should use
GPT vs MBR: Partition table overview. GPT (GUID Partition Table) and MBR (Master Boot Record) are abbreviations you will see a lot if you're embarking on creating a new drive partition on your PC or Mac. But it's small potatoes, really. We are going to... Read More




Advertisement

10 ways you can improve security of your Facebook account
Facebook has been hit by privacy scandles over the past 2 years. There was the Cambridge Analytica saga, the recently the security breach among others. Facebook confirmed that millions of users had their personal data accessed during a serious security breach disclosed late last month.... Read More

Why software updates are not always a good thing
In tech, we always advise people to strive and run the very latest version of given software. Be it, Android, be it Windows, Antivirus, apps, everything. It is a healthy habit with its own set of perks including; bug fixes that could possibly be loopholes... Read More




5 tips to stay safe from Bluetooth hacks and attacks
Sending files between devices over Bluetooth today sounds old school. It works over distances. It’s slower compared to newer and more improved technologies like WiFi. That’s how most people think about Bluetooth currently. But did you know that Bluetooth hacks and attacks are real? Below, we... Read More


Advertisement


Wi-Fi is adopting version numbers such as WiFi 6
The Wi-Fi Alliance, the standards body behind the infamous "Wi-Fi Certified" logo on basically every Wi-Fi enabled device out there, have since been the ones responsible for the naming of Wi-Fi protocols such as 802.11ab and 802.11n. See, if you have ever been in the... Read More

What is Aptx Bluetooth
One thing about cables is that they limit us to a specific area. Although, manufacturers have started releasing longer cables, wireless technology is an ideal way to transmit data over a long distance. The wireless technology is very dominant with Bluetooth. This has even developed... Read More
Advertisement
Advertisement